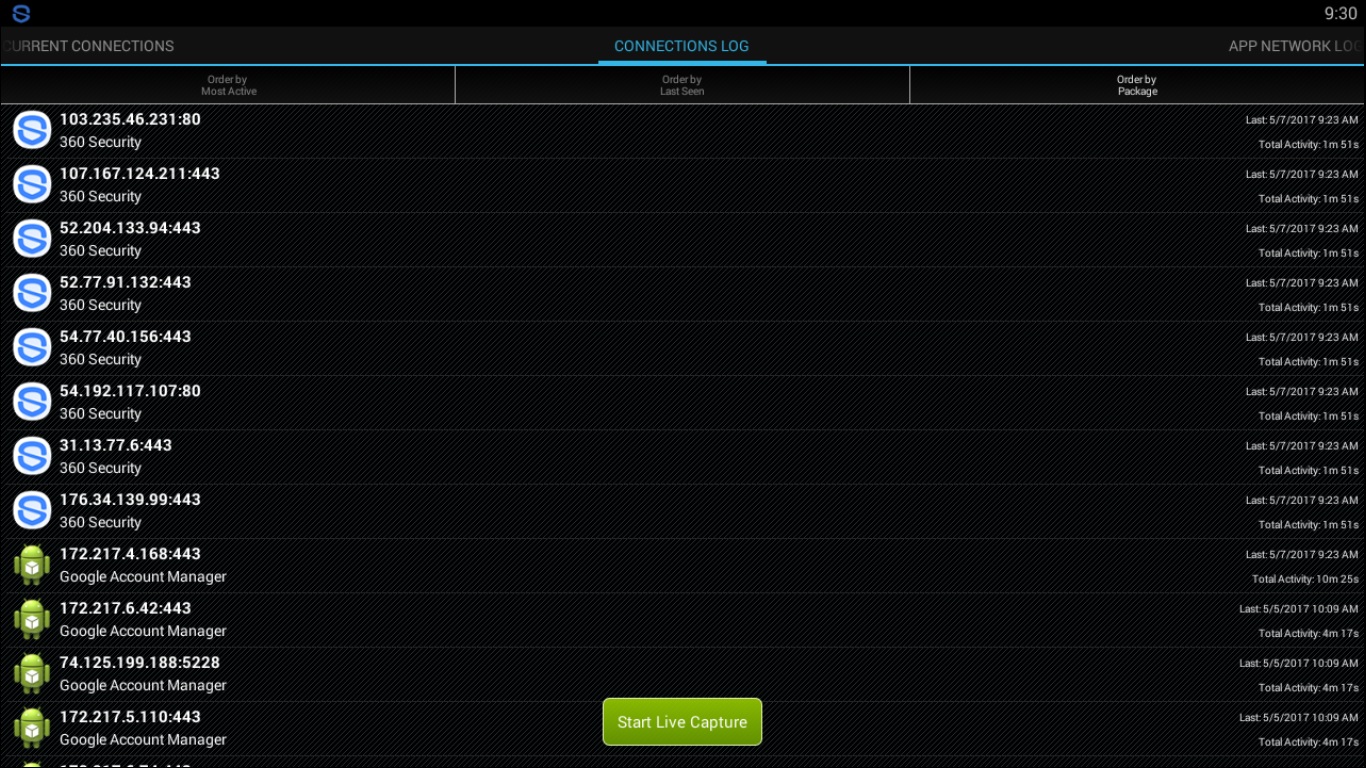
Hi Craig, As was suggested by Daniel (http://seclists.org/fulldisclosure/2017/May/9) , I installed the 360 Security app on BlueStacks Android emulator and captured HTTP packets exchanged by this app via Wireshark. Below is a screenshot from the Network Connections app running on BlueStacks showing the 360 Security connections that it was able to detect: From the Wireshark capture, following are the HTTP GET and GET response details for the IP addresses, along with their WHOIS links: 54.192.117.107: (https://whois.domaintools.com/54.192.117.107) 103.235.46.231: (https://whois.domaintools.com/103.235.46.231) Subsequently, I closed BlueStacks and re-opened it again and monitored the 360 security app connections via Network Connections app and HTTP packets via WireShark. Below is a screenshot from the Network Connections app showing the 360 Security connections that it was able to detect this time: From the Wireshark capture, following are the HTTP GET and GET response details for the IP addresses, along with their WHOIS links: 54.192.117.89: (https://whois.domaintools.com/54.192.117.89) 52.74.202.248: (https://whois.domaintools.com/52.74.202.248) 112.80.248.28: (https://whois.domaintools.com/112.80.248.28) 103.235.46.231: (https://whois.domaintools.com/103.235.46.231) As can be seen from the above screenshots from both the sessions the "lg=en&cn=us&vc=2284&uv=100&cid=104488&img_size=1&length=5&install_time=1494173731" string input as a parameter in the HTTP GET requests to update-cloud.i.360overseas.com IP addresses uniquely identifies the instance of 360 security app installed on the device and hence the device. So, anyone monitoring the insecure HTTP packets exchanged with update-cloud.i.360overseas.com IP addresses can easily track the IP addresses used by the device, which is a huge privacy risk. Also, the insecure HTTP packets exchanged with Baidu IP addresses in HongKong, bdimg.com IP addresses in China and update.i.360overseas.com IP addresses in Singapore expose the IP address used by the device as using the 360 security app, in those foreign countries. I think, this vulnerability deserves a CVE in the NVD database (https://nvd.nist.gov/vuln/search). The Wireshark packet captures for both the sessions are attached below. Thanks. On Sun, May 7, 2017 at 03:42 AM, Craig Young wrote: I would advise running a packet capture to see what data is sent. https://play.google.com/store/apps/details?id=app.greyshirts.sslcapture (https://play.google.com/store/apps/details?id=app.greyshirts.sslcapture) will let you do this from your device without root. -Craig On Thu, May 4, 2017, 5:10 PM seclists@xxxxxxxx (mailto:seclists@xxxxxxxx) wrote: I reinstalled the 360 security app on my phone to check the network connections it used & found via the Network Connections app that it did indeed use an insecure HTTP connection to exchange data with IP address 52.85.77.42 which is assigned to Amazon network(https://www.whois.com/whois/52.85.77.42 (https://www.whois.com/whois/52.85.77.42)). Attached is a screenshot from the network connections app showing this connection. From the 360 security app privacy policy page(http://www.360securityapps.com/m/en-us/about/privacy (http://www.360securityapps.com/m/en-us/about/privacy)) it can be seen that it uploads sensitive information about installed programs to a cloud security center. So, I am guessing that the above IP address corresponds to an Amazon cloud storage server. So, there is still a security hole in this App, where it may be transmitting sensitive system information via an unencrypted HTTP connection. Thanks. ----- Reply message ----- From: "Daniel Wood" To: Cc: Subject: [FD] 360 security android app snoops data to China Unicom network via insecure HTTP Date: Sun, Apr 30, 2017 6:26 AM Can't you just run the app in an Android emulator and shark it? Sent from my iPhone > On Apr 30, 2017, at 06:02, seclists@xxxxxxxx (mailto:seclists@xxxxxxxx) > wrote: > > I have a further update on the issue. After uninstalling the 360 security > android app, I found after repeated checks of Network Info on my phone via > the Ping & DNS app that even then the HTTP connection to IP address > 123.125.114.8 still frequently showed up. So, I monitored the network > connections on my phone via the Network Connections app > (https://play.google.com/store/apps/details?id=com.antispycell.connmonitor > (https://play.google.com/store/apps/details?id=com.antispycell.connmonitor)) > and found that this time the HTTP connection to IP address 123.125.114.8 was > being established by the ES File Explorer app > (https://play.google.com/store/apps/details?id=com.estrongs.android.pop > (https://play.google.com/store/apps/details?id=com.estrongs.android.pop) > (https://play.google.com/store/apps/details?id=com.estrongs.android.pop) > (https://play.google.com/store/apps/details?id=com.estrongs.android.pop))). > So, it is possible that the insecure HTTP connection to the above IP address > that I observed when both the 360 security and ES File Explorer app were > installed on my phone was in fact because of the ES File Explorer app or the > other possibility is that both the apps have the same problem. I haven't had > a cha > nce to re-install the 360 security app without the ES File Explorer to check > that and I don't intend to re-install the 360 security app on my phone, > since it anyways used to raise the temperature on my phone suspiciously. So, > I will report this as an issue for the ES File Explorer app in a separate > email. > > Thanks. > Hi, > > I found the following review posted about the 360 security android app: > > https://play.google.com/store/apps/details?id=com.qihoo.security&reviewId=Z3A6QU9xcFRPSG1HSTRaSVdNelVWY3FhZk5zcFlFMnZKeXRKRHhhQUE4VU9pLWV4UFBxeHJ3Xy1ZZWU2bEpOLTg0eGxzczFCV0lkaWxxTHRzZTQ4RWxzU2c > > (https://play.google.com/store/apps/details?id=com.qihoo.security&reviewId=Z3A6QU9xcFRPSG1HSTRaSVdNelVWY3FhZk5zcFlFMnZKeXRKRHhhQUE4VU9pLWV4UFBxeHJ3Xy1ZZWU2bEpOLTg0eGxzczFCV0lkaWxxTHRzZTQ4RWxzU2c) > > (https://play.google.com/store/apps/details?id=com.qihoo.security&reviewId=Z3A6QU9xcFRPSG1HSTRaSVdNelVWY3FhZk5zcFlFMnZKeXRKRHhhQUE4VU9pLWV4UFBxeHJ3Xy1ZZWU2bEpOLTg0eGxzczFCV0lkaWxxTHRzZTQ4RWxzU2c > > (https://play.google.com/store/apps/details?id=com.qihoo.security&reviewId=Z3A6QU9xcFRPSG1HSTRaSVdNelVWY3FhZk5zcFlFMnZKeXRKRHhhQUE4VU9pLWV4UFBxeHJ3Xy1ZZWU2bEpOLTg0eGxzczFCV0lkaWxxTHRzZTQ4RWxzU2c)) > "Snoops data to China Unicom via insecure HTTP link! Found while checking > Network info on my device with this app installed that it had established an > insecure HTTP connection to an IP address(123.125.114.8) on Chinese state > owned China Unicom network (China Unicom owns a stake in app developer via > Qihoo 360). Also, when installed, found my phone temperature rising > frequently indicating covert data transfer from my phone. I've now > uninstalled this Chinese spying app & advice the same to anyone using the > app. Resp to comment: updated above info with IP addr. > 360 Mobile Security Limited April 26, 2017 Hi, sorry for the inconvenience. > It will be helpful for us to solve the problem, if you can give us more > information and details . Attaching some screenshots would be helpful. > Please contact us by email: jenny@xxxxxxxxxxxxx (mailto:jenny@xxxxxxxxxxxxx) > (mailto:jenny@xxxxxxxxxxxxx (mailto:jenny@xxxxxxxxxxxxx)). Many thanks." > > I observed the same behavior when I had this app installed on my smartphone. > I checked the Network Info on my phone when this app was installed, using > the Ping & DNS > app(https://play.google.com/store/apps/details?id=com.ulfdittmer.android.ping > (https://play.google.com/store/apps/details?id=com.ulfdittmer.android.ping) > (https://play.google.com/store/apps/details?id=com.ulfdittmer.android.ping > (https://play.google.com/store/apps/details?id=com.ulfdittmer.android.ping))) > and found the insecure HTTP connection to the above IP address. After I > uninstalled the app, the HTTP connection to the above IP address was gone, > as well. On checking the WHOIS > info(https://www.whois.com/whois/123.125.114.8 > (https://www.whois.com/whois/123.125.114.8) > (https://www.whois.com/whois/123.125.114.8 > (https://www.whois.com/whois/123.125.114.8))) for this IP address it can be > seen that it is indeed on the Chinese state-owned China Unicom network. I > had App usage tracking permission on Android enabled for this app, to > facilitate phone temperature reduction, when I observed the above. > > Can other security researchers please check and comment on this security > hole? > > Thanks. > > _______________________________________________ > Sent through the Full Disclosure mailing list > https://nmap.org/mailman/listinfo/fulldisclosure > (https://nmap.org/mailman/listinfo/fulldisclosure) > Web Archives & RSS: http://seclists.org/fulldisclosure/ > (http://seclists.org/fulldisclosure/) _______________________________________________ Sent through the Full Disclosure mailing list https://nmap.org/mailman/listinfo/fulldisclosure (https://nmap.org/mailman/listinfo/fulldisclosure) Web Archives & RSS: http://seclists.org/fulldisclosure/ (http://seclists.org/fulldisclosure/)
Attachment:
360_security_HTTP_2.pcapng
Description: Binary data
Attachment:
360_security_HTTP_1.pcapng
Description: Binary data
_______________________________________________ Sent through the Full Disclosure mailing list https://nmap.org/mailman/listinfo/fulldisclosure Web Archives & RSS: http://seclists.org/fulldisclosure/