[Date Prev][Date Next][Thread Prev][Thread Next][Date Index][Thread Index]
[FD] [CVE-2015-6942] CoreMail XT3.0 Stored XSS
- To: fulldisclosure <fulldisclosure@xxxxxxxxxxxx>
- Subject: [FD] [CVE-2015-6942] CoreMail XT3.0 Stored XSS
- From: "shack.li" <shack.li@xxxxxxxxxxxxxxxxxxxx>
- Date: Fri, 27 Nov 2015 09:21:39 +0800
Application: CoreMail
Versions Affected: XT3.0
Vendor URL: http://www.coremail.cn/
Bugs: Stored XSS
Author:shack.li(DBAPPSecurity Ltd)
Description:
Coremail mail system was born in 1999, is widely used in network operators,
large enterprises, government institutions, colleges and universities and other
mail systems, so far, the user has more than 700000000,the official website.
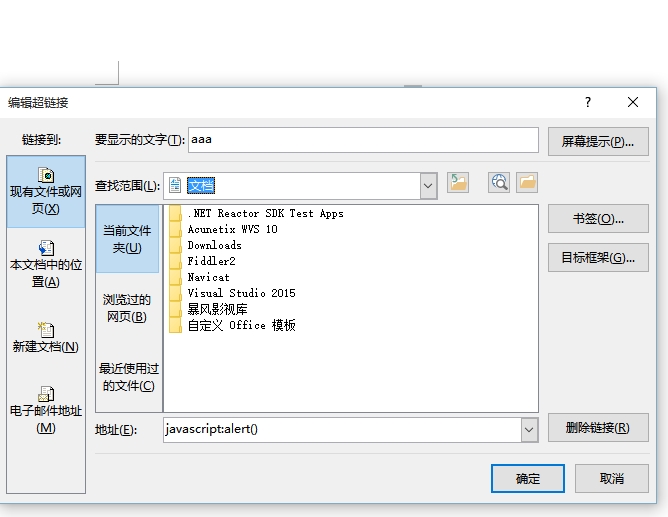
Create a document, insert a hyperlink, hyperlink for executing the JavaScript
test code "javascript:alert ()".
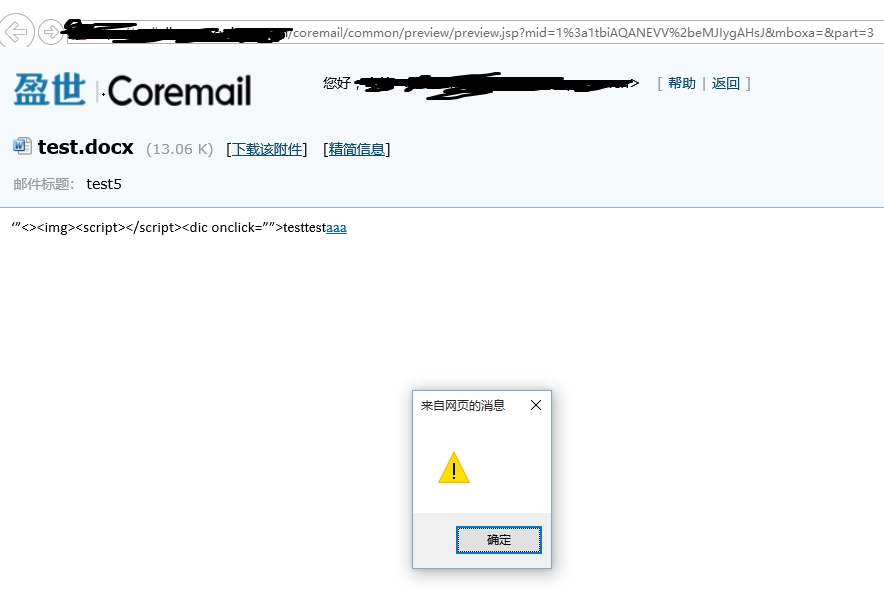
Then create a mail and upload attachments, and then send them to the other
users who need them. When other users online preview documents, click the
hyperlink, Attack code will be executed
step one:
step two:
----------------------------------------------------------------------------------------------------------------------------------
E-mail:shack.li@xxxxxxxxxxxxxxxxxxxx
DBAppSecurity Ltd
www.dbappsecurity.com.cn
_______________________________________________
Sent through the Full Disclosure mailing list
https://nmap.org/mailman/listinfo/fulldisclosure
Web Archives & RSS: http://seclists.org/fulldisclosure/
