[Date Prev][Date Next][Thread Prev][Thread Next][Date Index][Thread Index]
Re: [FD] Major Internet Explorer Vulnerability - NOT Patched
- To: David Leo <david.leo@xxxxxxxxxxxx>, Joey Fowler <joey@xxxxxxxxxx>
- Subject: Re: [FD] Major Internet Explorer Vulnerability - NOT Patched
- From: Zaakiy Siddiqui <zaakiy@xxxxxxxxxxxxx>
- Date: Wed, 4 Feb 2015 23:46:19 +0000
Hi David,
Nice one…great find! And thanks Joey for confirming the bypass of
HTTP-to-HTTPS restrictions.
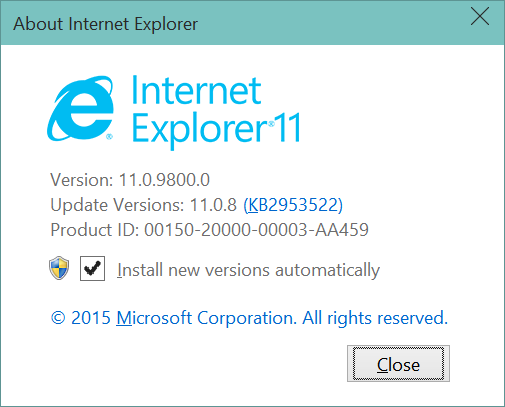
I can confirm that this also affects Spartan Browser (Experimental enabled in
about:flags in Internet Explorer 11).
I can also confirm that IE 10 is affected.
IE 9 appears to not be vulnerable. Screenshots below.
Regards,
Zaakiy Siddiqui
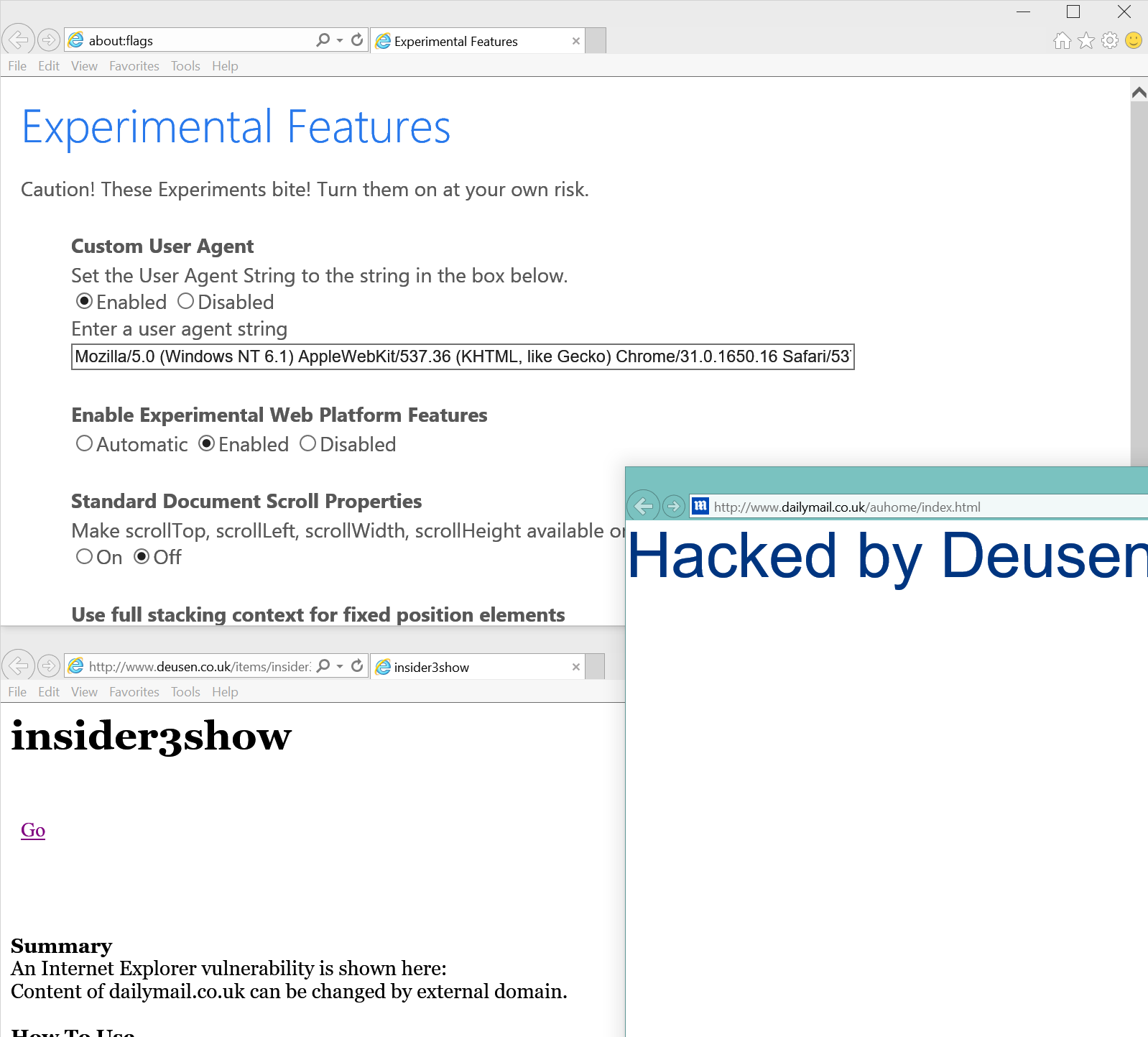
IE 11 Spartan - vulnerable (Windows 10)
[cid:Image1466.png@14b56f08dd75bb]
[cid:Image1487.png@14b56f6487b5d0]
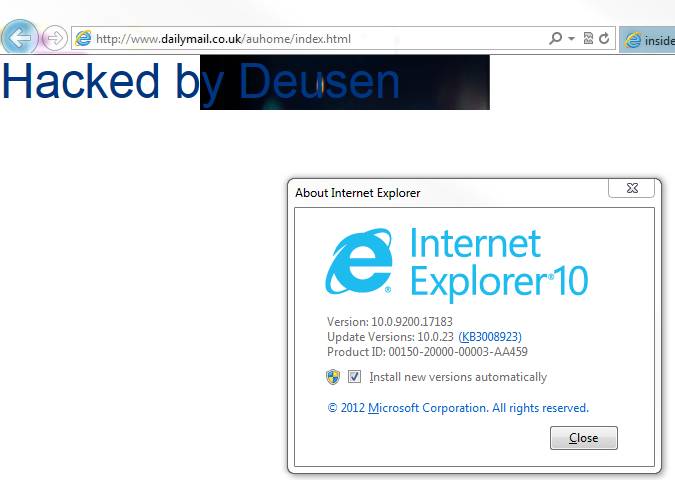
IE 10 - vulnerable (Windows 7)
[cid:Image1485.jpg@14b56f5f5025ce]
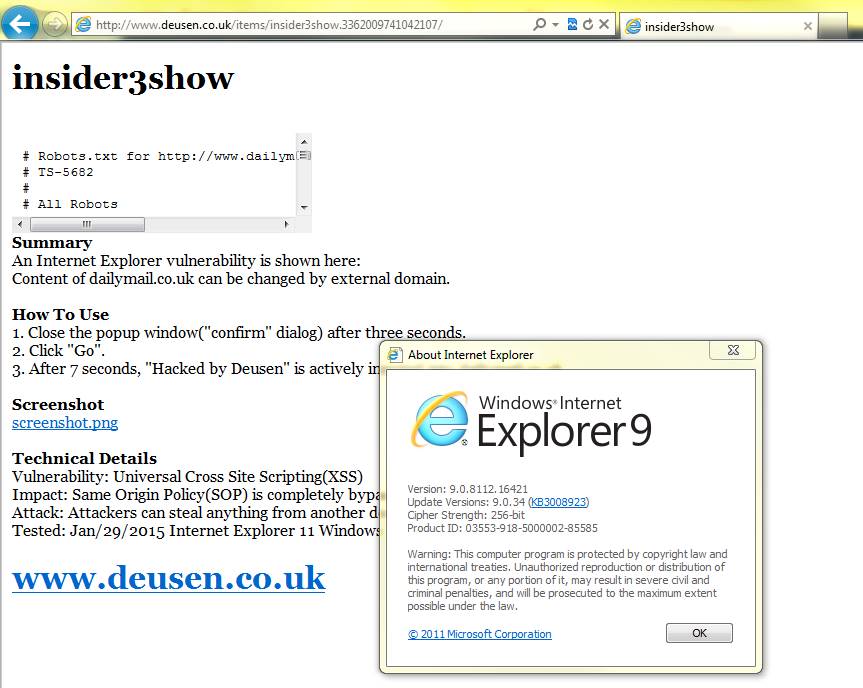
IE 9 - not vulnerable (Windows 7)
[cid:Image1503.jpg@14b56fa3c785e0]
From: David Leo<mailto:david.leo@xxxxxxxxxxxx>
Sent: Wednesday, 4 February 2015 11:13 PM
To: Joey Fowler<mailto:joey@xxxxxxxxxx>
Cc: bugtraq@xxxxxxxxxxxxxxxxx<mailto:bugtraq@xxxxxxxxxxxxxxxxx>,
fulldisclosure@xxxxxxxxxxxx<mailto:fulldisclosure@xxxxxxxxxxxx>,
bugs@xxxxxxxxxxxxxxxxxxx<mailto:bugs@xxxxxxxxxxxxxxxxxxx>,
cve-assign@xxxxxxxxx<mailto:cve-assign@xxxxxxxxx>
Microsoft was notified on Oct 13, 2014.
Joey thank you very much for your words.
Kind Regards,
On 2015/2/3 4:53, Joey Fowler wrote:
> Hi David,
>
> "nice" is an understatement here.
>
> I've done some testing with this one and, while there /are/ quirks, it most
> definitely works. It even bypasses standard HTTP-to-HTTPS restrictions.
>
> As long as the page(s) being framed don't contain X-Frame-Options headers
> (with `deny` or `same-origin` values), it executes successfully. Pending the
> payload being injected, most Content Security Policies are also bypassed (by
> injecting HTML instead of JavaScript, that is).
>
> It looks like, through this method, all viable XSS tactics are open!
>
> Nice find!
>
> Has this been reported to Microsoft outside (or within) this thread?
>
> --
> Joey Fowler
> Senior Security Engineer, Tumblr
>
>
>
> On Sat, Jan 31, 2015 at 9:18 AM, David Leo <david.leo@xxxxxxxxxxxx
> <mailto:david.leo@xxxxxxxxxxxx>> wrote:
>
> Deusen just published code and description here:
> http://www.deusen.co.uk/items/__insider3show.3362009741042107/
> <http://www.deusen.co.uk/items/insider3show.3362009741042107/>
> which demonstrates the serious security issue.
>
> Summary
> An Internet Explorer vulnerability is shown here:
> Content of dailymail.co.uk <http://dailymail.co.uk> can be changed by
> external domain.
>
> How To Use
> 1. Close the popup window("confirm" dialog) after three seconds.
> 2. Click "Go".
> 3. After 7 seconds, "Hacked by Deusen" is actively injected into
> dailymail.co.uk <http://dailymail.co.uk>.
>
> Technical Details
> Vulnerability: Universal Cross Site Scripting(XSS)
> Impact: Same Origin Policy(SOP) is completely bypassed
> Attack: Attackers can steal anything from another domain, and inject
> anything into another domain
> Tested: Jan/29/2015 Internet Explorer 11 Windows 7
>
> If you like it, please reply "nice".
>
> Kind Regards,
>
>
> _________________________________________________
> Sent through the Full Disclosure mailing list
> https://nmap.org/mailman/__listinfo/fulldisclosure
> <https://nmap.org/mailman/listinfo/fulldisclosure>
> Web Archives & RSS: http://seclists.org/__fulldisclosure/
> <http://seclists.org/fulldisclosure/>
>
_______________________________________________
Sent through the Full Disclosure mailing list
https://nmap.org/mailman/listinfo/fulldisclosure
Web Archives & RSS: http://seclists.org/fulldisclosure/
